Message Authentication Codes
… to help with integrity
… and to survive CCAs
- secrecy
- integrity
- authenticity
Why is integrity desireable?
- Solves message tampering
- Does not solve replayability
- It helps with CCAs…
No integrity in stream ciphers
No integrity in block ciphers
In CBC a change to block only affects . is a number? Scramble it!
Flipping a bit in the flips a bit in .
We send .
A mac-scheme is very much like an encryption-scheme.
Canonical verification
Watch out for timing attacks in strcmp
Mac-forge experiment
:
- A key k is generated by running .
- The adversary is given input and oracle access to . The adversary eventually outputs . Let denote the set of all queries queries that asked its oracle.
- succeeds if and only if and . In that case the output of the experiment is defined to be 1.
Definition 4.2
A message authentication code is existentially unforgeable under an adaptive chosen-message attack, or just secure, if for all probabilistic polynomial-time adversaries there is a negligible function such that:
Mac-sforge experiment
:
- A key k is generated by running .
- The adversary is given input and oracle access to . The adversary eventually outputs . Let denote the set of all queries that asked its oracle, along with the response.
- succeeds if and only if and . In that case the output of the experiment is defined to be 1.
Definition 4.3
A message authentication code is strongly secure, or a strong MAC, if for all probabilistic polynomial-time adversaries , there is a negligible function negl such that: here is a negligible function such that:
Constructing Secure MACs
Construction 4.5
Let F be a pseudorandom function. Define a fixed-length MAC for messages of length n as follows:
-
: on input a key and a message , output the tag . (If then output nothing.)
-
: on input a key , a message , and a tag , output 1 if and only if . (If , then output 0.)
Theorem 4.6
If is a pseudorandom function, then Construction 4.5 is a secure fixed-length MAC for messages of length .
or:
Proof
We use the proving strategy of analyzing the scheme using truly random functions, and then proving that the security loss incurred by using pseudo-random functions insead is negligible.
Let and denote the scheme from construction 4.5, except that uses a truly random function instead of
It follows that
Because directly applies , and because for any message , the value is uniformly distributed in from the point of view of the adversary .
From
It follows that if
(4.2)
then
Proof by Distinguisher
- Run . Whenever queries its MAC oracle on a message m (i.e., whenever requests a tag on a message ), answer this query in the following way: Query with m and obtain response t; return to .
- When outputs at the end of its execution, do:
- Query with and obtain response .
- If (1) and (2) never queried its MAC oracle on , then output 1; otherwise, output 0.
Proof by Distinguisher
Since the view of inside is distributed identically to that of in , and since exactly when :
and
and
Gives
Since runs in polynomial time.
Hence equaion (4.2) is proven!
Problem:
Construction 4.5 only works for small messages; same length as the key!
We can fix that. For a message of -length blocks, let
Then use as the tag of .
More Problems:
-
Re-ordering attack
Solved by adding to -
Truncation attack
Solved by adding message length to -
Mix ‘n’ match Solved by adding a random message id to
We get:
This is impractical. The message length is still fixed, and the message-space got a lot smaller.
CBC-MAC
A clever solution to those three problems
Construction 4.11
Let be a pseudorandom function, and fix a length function . The basic CBC-MAC construction is as follows:
- : on input of key and a message of length , do the following (we set in what follows):
- Parse as where each is of length .
- Set . Then for :
Set
Output as the tag.
- : on input a key , a message , and a tag , do: If is not length then output . Otherwise, output if and only if
(Length check + canonical verification.)
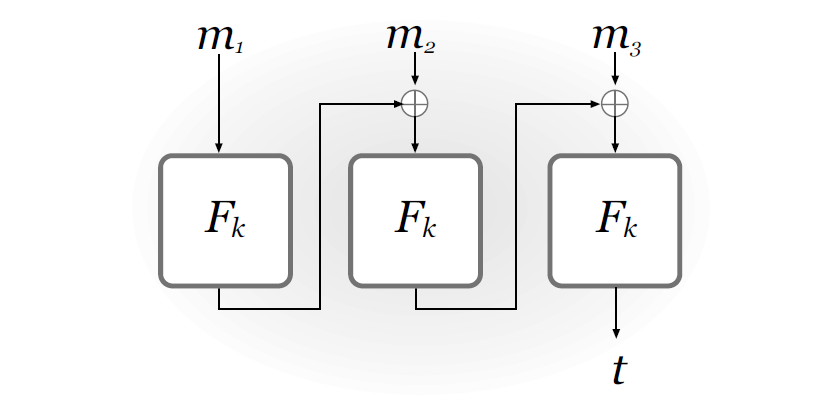
Is it ordering attack safe?
Is it truncation attack safe?
Is it mix ‘n’ match attack safe?
New problem: prefix attack
(This scales to arbitrary length messages.)
Prefix attack solution
Prefix the length:
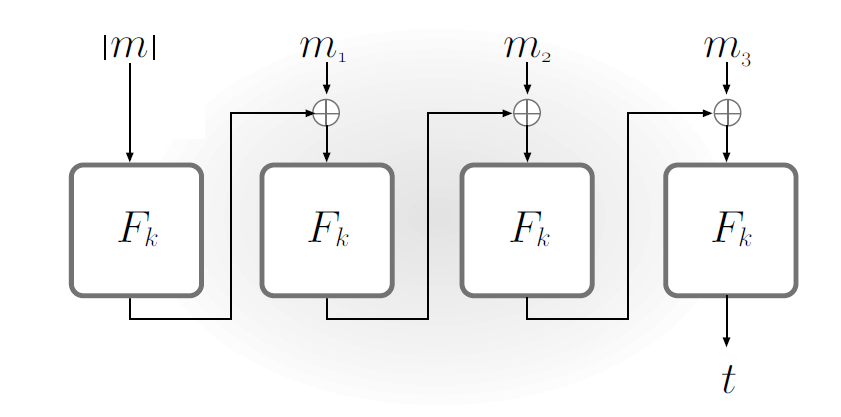
(hold on to your horses)
CBC-MAC
Proof of Security
“intended for advanced readers.”
is a keyed function that, for security parameter , maps -bit keys and -bit inputs to -bit outputs.
is a keyed function that, for security parameter , maps -bit keys and inputs in to -bit outputs.
Exactly like CBC-MAC, but without a fixed length-function ( may vary).
A set of strings is prefix-free if it does not contain the empty string, and no string is a prefix for any other string .
Theorem 4.13
If is a pseudorandom function, then is a pseudorandom function on prefix-free inputs: for all probabilistic polynomial-time distinguishers that query their oracle on a prefix-free set of inputs, there is a negligible function such that:
,
where is chosen uniformly from and is chosen uniformly from the set of functions mapping to .
We can make work as a pseudorandom function for arbitrary-length inputs by converting these inputs to belong to the proper input space.
To get a tag from arbitrary length message :
This is based on theorem 4.6, for secure fixed-length MACs. It works because ensures that the messages are unique.
How do we implement ?
(a) Fix the length , and then simply:
(b) Prepend the length:
where pads a message with 0s until it has the valid block length.
We want to prove that the security of depends solely on the security of .
First, we replace in with a random function that maps -bit inputs to -bit outputs for security parameter .
We need to show: if is chosen uniformly in , then is indistinguishable from a random function mapping to -bit strings, as long as the set of inputs queried is prefix-free.
Claim 4.14
Fix any . For all distinguishers that query their oracle on a prefix-free set of inputs, where the longest input contains blocks, it holds that:
where is chosen uniformly from , and is chosen uniformly from the set of functions mapping to .
Notice that for any it holds:
Proof of claims 4.14-15
First we show that is smooth. Then we show that smoothness implies claim 4.14.
Fix some .
Let be a prefix-free set of inputs .
Let be the length (in blocks) of the longest input .
We define smoothness:
is -smooth if for every and every , it holds that:
with the probability uniform over choice of .
We will show that is -smooth for . (Claim 4.15)
denotes the set of inputs on which is evaluated during the computation of for any with and .
Now let’s look at two different messages with a different number of blocks:
There is a non-trivial collision if for and it holds that , but .
There is a non-trivial collision in if for and it holds that , but
Let be the event that such a collision occurs.
With no non-trivial collision:
We choose each output value for for a given input the first time it is requested. Each time, we choose it randomly. (Not efficient, but very uniformly chosen.)
Fun fact: We do not need to choose and to determine if there is a collision: If the last elements collide it can only be because is a prefix of , but is prefix-free.
No non-trivial collision occurs.
All values fixed by , including are uniform and independent of each other.
This means that or any :
Let us find an upper bound for :
is a collision between or within any fixed . So is the union of all for all within the length of (up to ). (All unique collisions between or within inputs.)
Using union-bound:
Let us find upper bound for :
Probability of any collision is larger with longer inputs, so we fix two inputs with length (max length).
Fix as the largest integer such that .
- For fix uniformly. (steps to )
- Fix uniformly. (step )
- For choose uniformly. (steps to )
- For choose uniformly. (steps to )
is the event that a non-trivial collision occurs by step .
Probability of collision first at step is (attempts over block space).
Probability of collision first at step is (2 values: 2 times attempts over block space).
Probability of collision first at step is . (attempts + 1 over block space) [why?]
Recall

Authenticated encryption
Secrecy and integrity
Definitions
:
-
Run to obtain a key
-
The adversary is given input and access to an encryption oracle . The adversary outputs a ciphertext .
-
Let , and let denote the set of all queries that asked its encryption oracle. The output of the experiment is 1 if and only if (1) and (2) .
Definition 4.16
A private-key encryption scheme is unforgeable if for all probabilistic polynomial-time adversaries , there is a negligible function such that:
Definition 4.17
A private-key encryption scheme is an authenticated encryption scheme if it is CCA-secure and unforgeable.
This is the strongest security definition yet!
Generic constructions
Goal: Come up with a construction that combines any CPA-secure encryption scheme with any unforgeable to achieve authenticated encryption.
Given , , come up with ciphertext and tag .
Three obvious constructions:
-
Encrypt and authenticate
, -
Authenticate then encrypt
, -
Encrypt then authenticate
,
1. Encrypt and authenticate
,
Nope.
Unforgabilty does not guarantee secrecy; may leak information about
2. Authenticate then encrypt
,
Nope.
Mumble mumble, padding oracle attack, mumble mumble
3. Encrypt then authenticate
,
Yes!
Construction 4.18
Let be a private-key encryption scheme and let be a message authentication code, where in each case key generation is done by simply choosing a uniform -bit key. Define a private-key encryption scheme as follows:
Construction 4.18
-
: on input , choose independent, uniform and output the key .
-
: on input a key and a plaintext message , compute and . Output the ciphertext .
-
: on input a key and a ciphertext , first check whether . If yes, then output ; if no, then output .
Intution:
- Since ‘ing is the final step, unforgeability is implied!
- Since an adversary cannot hope to forge a valid ciphertext, the CCA decryption oracle is useless; CPA implies CCA!
Theorem 4.19
Let be a CPA-secure private-key encryption scheme, and let be a strongly secure message authentication code. Then Construction 4.18 is an authenticated encryption scheme.
Strategy:
Show that strong security of implies that any “new” ciphertexts submitted by will be invalid.
Definitions:
- a ciphertext is , if did not receive it from the encryption oracle
- is the event that submits a , valid, to the decryption oracle.
Claim 4.20
is negligible
Proof of 4.20
Intuitively (again): If can forge a valid ciphertext, it has beaten
Proof of 4.20
Formally: We construct an adversary attacking by running a a adversary .
Let be a polynomial upper-bound on the number of decryption-oracle queries made by
- Choose uniform and .
- Run on input . When makes an
encryption-oracle query for the message , answer it as follows:
- Compute c ← EnckE(m).
- Query to the MAC oracle and receive in response. Return to .
The challenge ciphertext is prepared in the exact same way (with a uniform bit chosen to select the message mbthat gets encrypted).
When makes a decryption-oracle query for the ciphertext answer it as follows: If this is the ith decryption-oracle query, output (c, t).j0 Otherwise:
- If was a response to a previous encryption-oracle query for a message m, return m.
- Otherwise, return ⊥.
Information-Theoretic MACs
Can we have CCA-security without unforgeability?
Technically, yes.
But we won’t look into that.
Because unforgeability is an easy way to get CCA-security.